This phishing scam was sent to a public UMN Google Group with the subject 'Payroll Schedule'.
A version of the message is included below.
Indicators of Phishing
Embedded Link
The first thing to cause suspicion is the embedded link in the message. When you hover (remember to hover, not click!), you would see the URL embedded appears to be for a Panera Bread domain: t[.]e1[.]panerabread.com/[redacted]
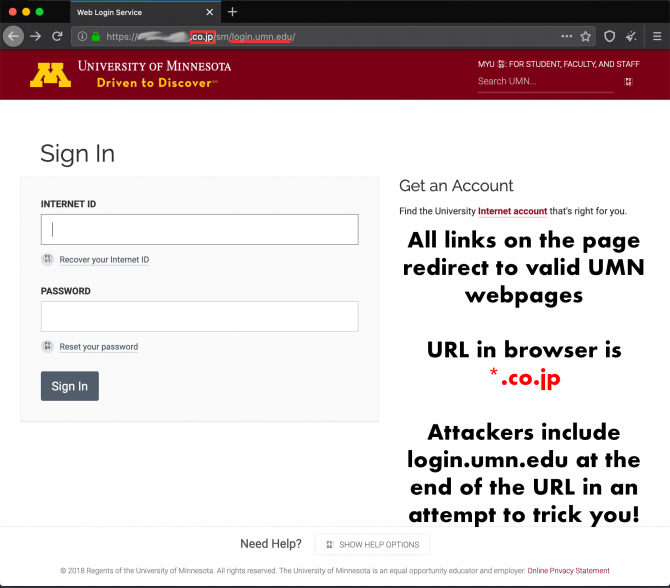
Disguised URL
The second thing to cause suspicion is the page that this redirects to. It is a very believable looking UMN login page, but the URL looks quite strange indeed!
URL of Login page: https://[redacted][.]co[.]jp/sm/login.umn.edu
The attackers tried to be clever by including 'login.umn.edu' in the URL and even went to the trouble of putting a security certificate on the site so you are able to connect to it using secure http (HTTPS).
However when you look closely, you will see that the URL is actually .co.jp!
Google Groups Settings
These attackers are great tricksters, and they are happy to use any publicly available resource, like UMN Google Groups, to reach a large audience.
Keep your eyes peeled for suspicious messages, and make sure to restrict your Google Group settings as much as is feasible for its purpose.
Stay safe, stay healthy, and if it sounds too good to be true, it probably is!