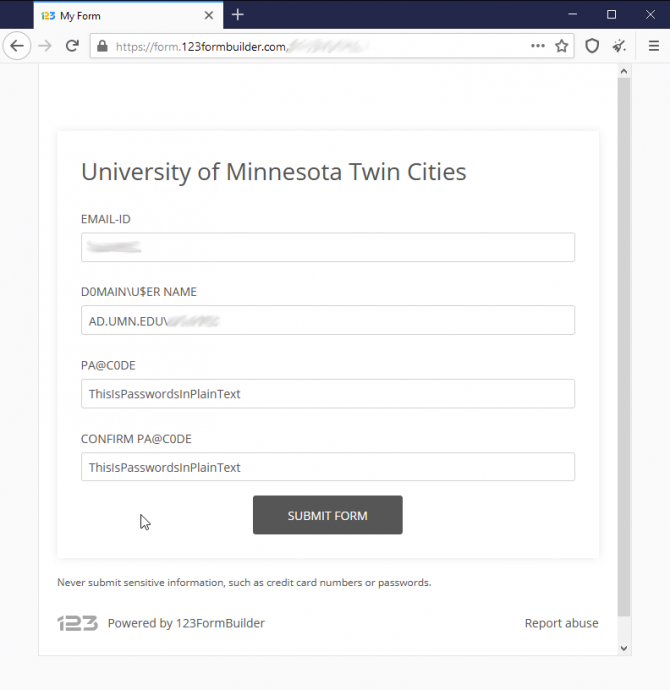
Scammers used a couple of common techniques in this example.
- They used a real, but compromised, email account to send this scam email that contains a link to a form requesting sensitive login information.
- They also obscured the form’s fields to evade spam filters that might be looking for forms asking for username and password.
Indicators of Phishing
- Generic greeting: “Hello user”
- From a hospital trust fund and non-UMN email address
- Sense of urgency: “last and final notice”
- The URL to the form is not umn.edu (form.123formbuilder.com)
- Passwords on the form are shown in plain text (see image)
- USER and PASSCODE obscured on the form (U$ER, P@CODE)
- To: a non-UMN email address
What to do if you receive one of these:
- Do not reply, click the link(s), or login (if you do click the link).
- Forward the scam email, with headers, to [email protected].
- Report it as phishing to Google. In Gmail, click the three-dot More menu next to Reply and choose Report phishing to help educate Google's filters to block similar messages in the future.
- For more information, please see: How to Manage Spam Emails
Example:
From: *Name Redacted (GREAT ORMOND STREET HOSPITAL FOR CHILDREN NHS FOUNDATION TRUST)* <[email protected]>
Date: Monday, June 21, 2021
Subject: UPDATE@University of Minnesota Twin Cities
To: "[email protected]" <[email protected]>
Hello user,
This is the last and final notice or our administrator will disable your access to your email. Please click here to University of Minnesota Twin Cities-IT_UPDATE <hxxps://form[dot]123formbuilder[dot]com/5936680/form> your account security by completing the required details to avoid the deactivation of your edu email account.
A cordial greeting,
IT Service Desk (c)2021.