
Manage External Vulnerability Scans for PCI DSS
Coalfire/Rapid7 External ASV is the vulnerability scanner used to discovery map and scan systems and devices that are in-scope for the PCI DSS external vulnerability scan and map requirement. Items in-scope include any system or device which processes, stores, transmits, or has the ability to impact the security of cardholder data.
An external vulnerability scan is required after any significant changes (e.g., new system component installation, change in network topology, firewall rule modification, product upgrade).
This document provides responsibilities and instructions on how Coalfire/Rapid7 discovery scanning, vulnerability scanning, false postive tracking, and reporting is used at the University of Minnesota by units for PCI DSS external vulnerability scans and maps. Units manage the external vulnerability scans for PCI DSS for their area.
Understand Your Responsibilities
- Maintain the list of IP addresses of of systems and devices that are in-scope and on the University network in your designated Coalfire ASV Project. Include servers, workstations, terminals, printers, network infrastructure, and other devices. Email [email protected] with changes.
- Review the external vulnerability scan of all IP addresses in the ASV Project at least monthly.
- Schedule a follow up scan for IP addresses that were not alive during the scan for when these devices are on-line.
- Remediate vulnerabilities dectected. Mitigation could include applying a patch, changing the configuration, applying compensating controls, or documenting as a false positive
- Fix and mitigate the vulnerabilities flagged as Compliance FAIL.
- Fix and mitigate the other vulnerabilities.
- Run another vulnerability scan to verify that the vulnerabilities are mitigated.
- Document mitigation plans, compensating controls, vulnerability disputes and special hosts.
- Send documentation to support a dispute to University Information Security at [email protected] with subject PCI External Scan Dispute Request. Include the IP address of the asset. University Information Security group will review your request and respond. Coalfire will review the dispute and evidence provided. If Coalfire approves the dispute, the dispute is only good for the current quarter, even when it was submitted and approved the last month of the previous quarter.
- Send documentation to support a special host to University Information Security at [email protected] with subject PCI External Scan Special Host Request. Include the IP address of the asset. University Information Security group will review your request and respond. Coalfire will review the special host documentation and determine if it is acceptable.
- Update your remediation plan/ mitigation strategy at least monthly for vulnerabilities detected.
- Update your configuration standards for new vulnerabilites remediated and patches as a result of the scans.
- Download quarterly reports to document your units attestation of compliance with PCI DSS external vulnerability scanning. Quarterly cycle is February, May, August, and November.
- Download Attestation of Scan Compliance (AoSCPlusIPTargets) report.
- Download Detailed report.
- Download Summary report.
- Download Remediation Tracking report.
Using CoalfireOne
Sign In
Coalfire/Rapid7 External-ASV (authentication required)
Viewing the Scan Schedule
- Select Setup in the left navigation menu.
- Select the name (e.g., Arboretum, Parking, OIT Infrastructure, U of MN).
- Select Targets to see the list of hosts included in the scan.
All hosts are scheduled for monthly scans. Notify University Information Security ([email protected]) if you need to change the schedule or list of hosts.
Reviewing the Compliance Status of each Host
- Select Analyze in the left navigation menu.
- Select Hosts.
Reviewing the Scan Results
- Select Analyze in the left navigation menu.
- Select Vulnerabilities.
- Use the filter (e.g., ASV VULNERABILITIES, ALL VULNERABILITIES).
- Select the vulnerability to view the impact and remediation.
Must immediately remediate the vulnerabilities flagged FAIL in the compliance column.
Scheduling Rescan of Host
- Select Analyze in the left navigation menu.
- Select Hosts.
- Select the IP address(es).
- Click on the 3 vertical dots next to the X.
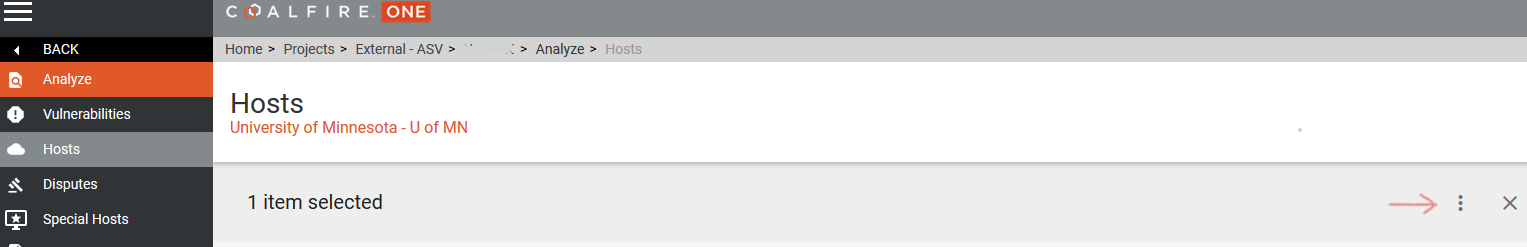
- Select rescan.
Generating Reports
- Select Analyze in the left navigation menu.
- Select Hosts.
- Select the + icon that looks like a piece of paper.
- Use the pull down to add the reports to generate.
- Select generate.
Viewing and Downloading Reports
- Select Reports in the left navigation menu.
Attestation reports are listed under Reports. Select the Custom Report View for the quarter (e.g., 2019-11 Quarterly Report).
For questions, contact University Information Securtiy.
Content Last Reviewed: November 2019 by University Information Security
More Information
- Payment Card Information Consultation
- Technical Vulnerability Management standard-Information Security Policy
- Manage Internal Vulnerability Scans for PCI DSS