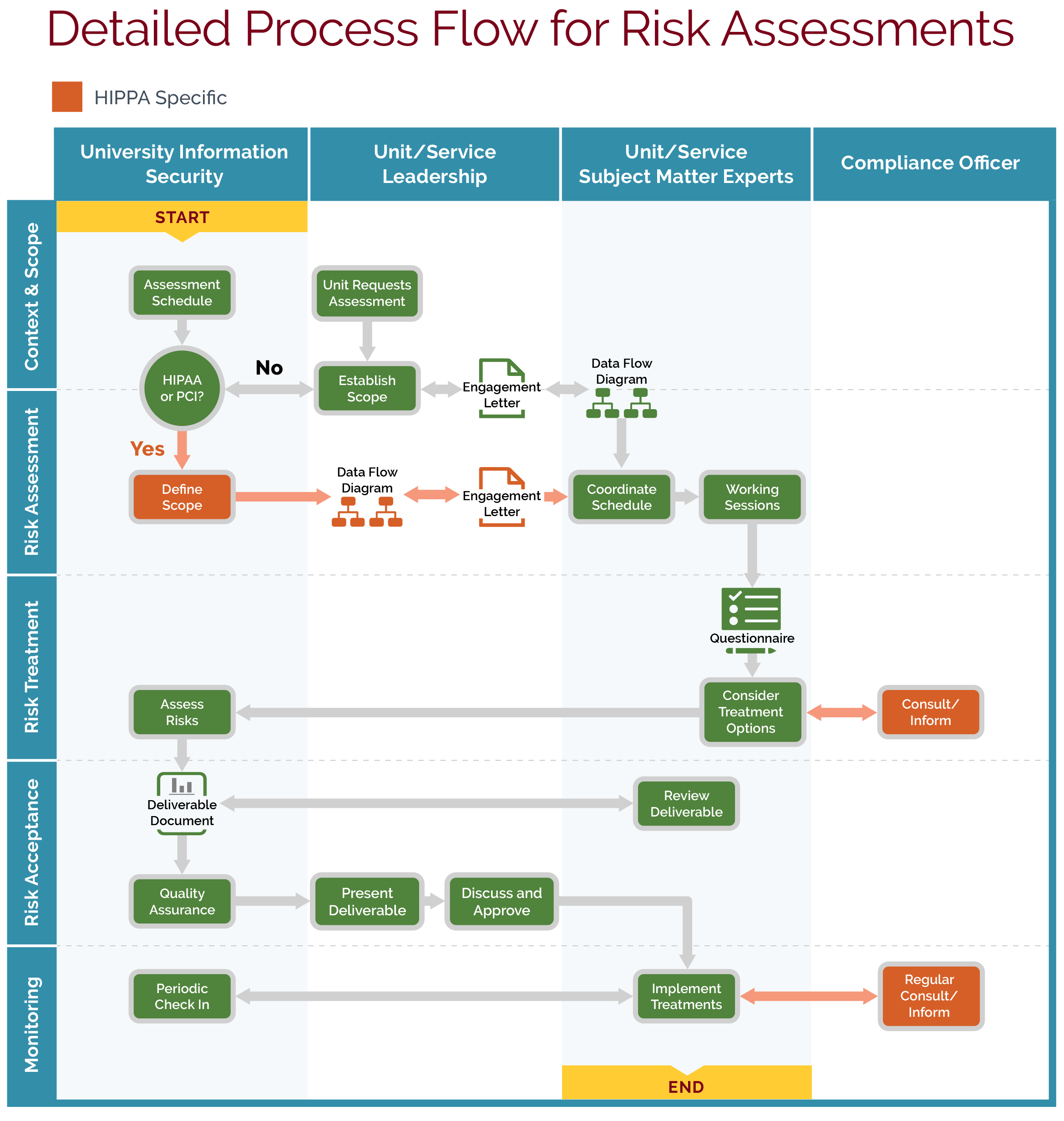
Collaborate on a Risk Assessment
Information security risk assessments for a unit, program, application, or service are based on statutory or regulatory requirements (including FISMA, HIPAA or PCI-DSS) and/or industry best practices (including ISO 27000 or NIST 800-53 frameworks) in order to:
- Identity the scope of private data
- Assist units in evaluating risks and treatment options
- Determine that data is handled and disposed of appropriately
- Plan risk treatment plans
- Apply security standards appropriately and consistently.
Assessments conducted by University Information Security are funded by the Information Security Risk Management Program, employ consistent University criteria and are scheduled based on level of risk.
Request a Risk Assessment
University faculty or staff can email [email protected] to request a risk assessment for a unit, program, application, technology platform or service. The request is evaluated based on the prevalence of private data as identified, critical services (such as life and safety) and potential impact to the University. The scope and priority of the assessment are reviewed with the Risk Acceptor (usually a Dean, Vice President or other senior leader).
Prepare for a Risk Assessment
Units can prepare by reviewing the information security standards, identifying and prioritizing gaps in current processes and communicating the schedule and expectations to staff.
Regardless of participating in a risk assessment, units are required to conduct a gap analysis between current practices and the information security standards, and to develop a plan to prioritize and manage risk treatment efforts for any gaps identified.
Participate in a Risk Assessment
The time commitment for a risk assessment varies based on scope and complexity. The process typically involves a series of collaborative meetings between the unit's subject matter experts and University Information Security risk analysts working through the following phases:
- Establish Scope and Context
- Assess Risks
- Plan Risk Treatments
- Accept Risk
- Monitor Treatments.
Risk Treatment Options
Risk treatment plans are collaboratively discussed and may include:
- Treatment: implementing controls to reduce the likelihood and/or impact of risk to an acceptable level.
- Transfer: outsourcing or otherwise transferring all or a portion of the risk, or purchase insurance. If a department or unit is an IT Service customer, some portion of risk ownership may be transferred to the IT Service, e.g. platform-level infrastructure, but the department or unit continues to be responsible for application-level risks.
- Avoidance: ceasing a high risk function or activity.
- Acceptance: making an informed decision to tolerate a certain level of risk by weighing the likelihood and impact of risk against the resources required to mitigate it.
Deliverable
The Risk Assessment document includes risks identified and risk treatment plan(s) as a foundation for future risk management by the unit. Supplemental documents may include data diagrams or relevant guideline material. The Risk Assessment document is classified as University Private-Restricted data.