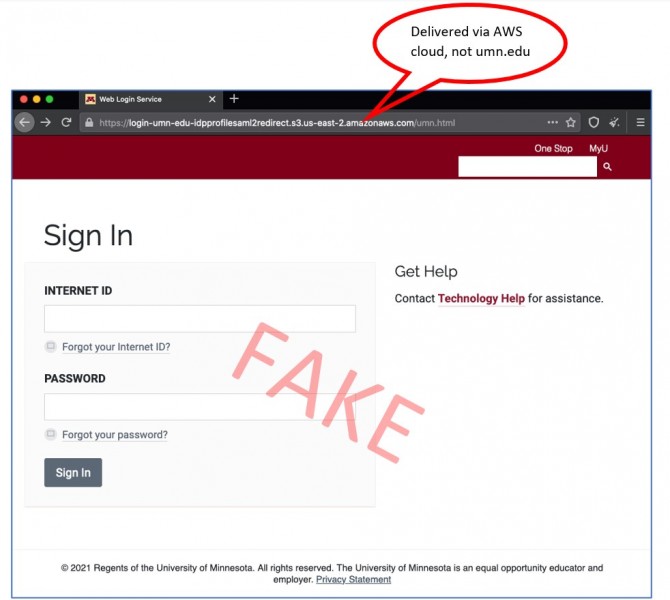
Scams involving fake login pages practically disappeared after the University implemented Duo two-factor authentication for University staff and students.
Now the fake login pages are back, typically delivered as a link in a scam email. Scammers are capturing ID and password combinations so they can try to trick people into approving a Duo push they did not initiate. See a recent example below.
What to do if you receive one of these:
- Do not reply, log in, or click the link(s).
- Forward the scam email, with headers, to [email protected].
- Report it as phishing to Google. In Gmail, click the three-dot More menu next to Reply and choose Report phishing to help educate Google's filters to block similar messages in the future.
- For more information, please see: How to Manage Spam Emails
Example
Subject: Case CS0030147 umn.edu
Date: Thu, 18 Feb 2021 06:58:09 -0600
From: "The University of Minnesota" <compromised account at another .edu>
Body of text:
Hi security
2 messages from umn.edu Admin Desk on Thursday, February 18, 2021 could not be delivered due to server error, you can read the messages and fix this error.
Preview Message Here hxxps://login-umn-edu-idpprofilesaml2redirect.s3.us-east-2.amazonaws.com/umn.html
**This is an automated message please do not reply**
Best regards,
Management
Th?s ?m??l w?s s?nt t? [email protected]