
Know Your Data and How to Protect University Data
It is important that you familiarize yourself with the types of data entrusted to you, how you are accessing the data, and how you are storing the data. You are required to adhere to the University’s security policies, laws, and contractual agreements for the type of data entrusted to you.
Challenge
Loss or unauthorized disclosure of private data can harm individuals and the University and may violate laws such as the Family Educational Rights and Privacy Act (FERPA) or the Health Insurance Portability and Accountability Act (HIPAA).
What do you need to do to follow the University requirements to protect the data that you access or use?
Solutions
It is important that you familiarize yourself with the types of data entrusted to you, how you are accessing the data, and how you are storing the data. You are required to adhere to the University’s Information Security Policy and the Data Security Classification Policy, laws, and contractual agreements for the type of data entrusted to you. Follow the steps below, if you use a personally-owned computer and/or device or are responsible for self-managing your University-provided computer and/or device.
Identify Your Data’s Security Classification
Identify the security level using the data security classification of the data you work with. Then, identify your data security level.
Identify Your Data’s Security Level
The University uses the following three security levels.
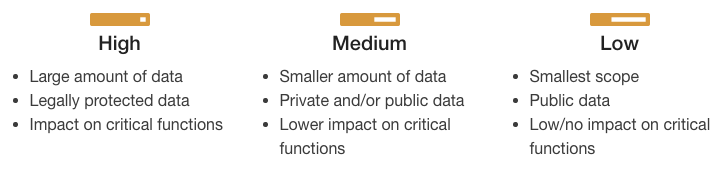
Use the Identifying Security Level appendix to determine the security level. Use the security level to identify the information security controls you are required to meet on the computer/device.
Apply the Information Security Standards
The information security standards define the most current controls required for each security level.
- Apply the Information Security standards on your computer/device.
- Periodically review the Information Security standards for updates.
Report Unauthorized Access or Disclosure Immediately
In the event of suspected unauthorized access to or disclosure of University data, contact [email protected]. The Report Information Security Incidents procedure provides more information.
Intended Audiences
Do-It-Yourself Resources
Resources
This University policy provides the University data security classification and helps you identify your security level for protecting the data.
Resources
This University policy provides the information security controls that are required to protect the data and University IT resources, and includes information on how to use the standards and request an exception.
Resources
This policy provides information about the Information Security Risk Management (ISRM) program, including identifying and tracking information security risks, developing plans for remediation, and providing guidance on...
Resources
This University policy provides information on how to report a suspected loss of private data, and includes information on the University process for notifying individuals of an information security breach.
Resources
Remind yourself and others about safe computing best practices by posting our handout.