
What is Email Spoofing? A Look at How the University Prevents Email Scams

By: Weston Crosley, Business Analyst, Team Lead - Drupal and Messaging / Calendaring Services (Office of Information Technology)
Have you ever been suspicious of an email claiming to come from the University of Minnesota that ends up in your inbox, or even your spam folder? Have you ever wondered how phishing attempts actually work, and what the University does to defend against them? As a large University, we are often the target for phishing and email scams, but we have preventive measures in place to protect you and your data, one of which is an outgoing email requirement called DMARC.
What is DMARC?
DMARC (Domain-based Message Authentication Reporting and Conformance) is an email verification system designed to protect the University of Minnesota’s “brand," or domain, @*umn.edu (i.e., r.umn.edu, morris.umn.edu, crk.umn.edu, d.umn.edu, or umn.edu). The verification system prevents attackers from using the brand to spoof emails for phishing, scams, and other cyber crimes.
Domain spoofing is one of the main ways that phishing emails are created, and it is what DMARC looks out for. Someone outside of the University who is trying to obtain personal data or other information will create an email address that “spoofs,” or imitates, the University’s domain to make emails look like they are coming from an @*umn.edu email address. Because email infrastructure isn’t perfect and can still be intentionally exploited, these spoofed emails can look very convincing. Therefore, it is important to keep email security and verification in mind. This is what DMARC is for.
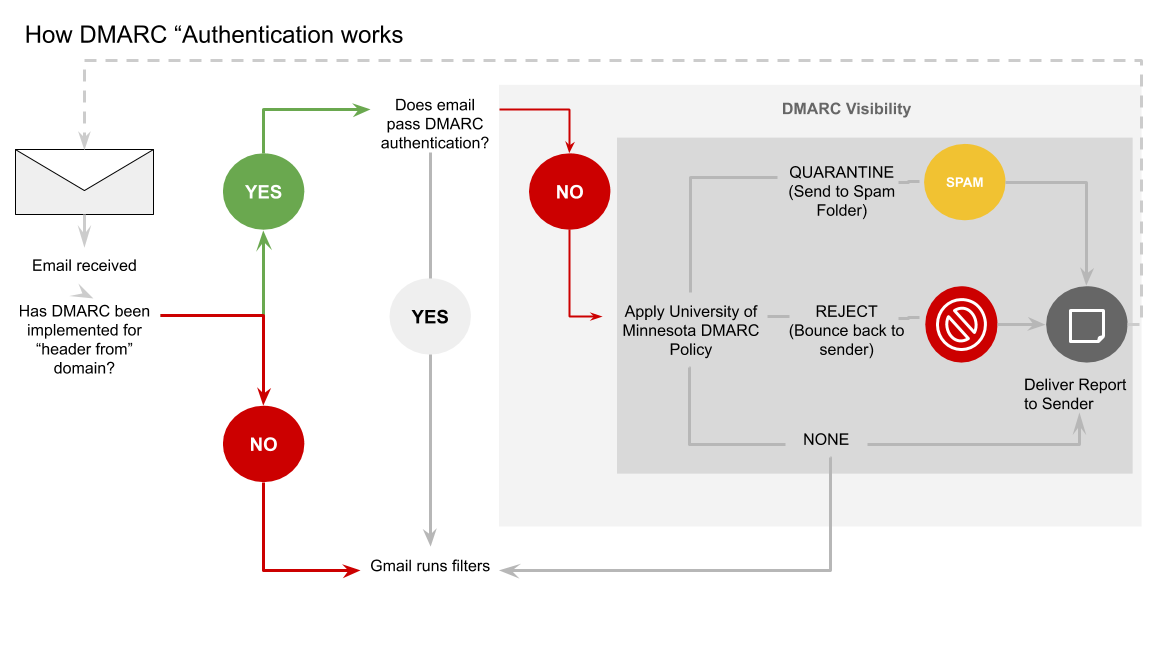
How Does DMARC Work?
Having a DMARC Policy
A DMARC policy is how we, as the University, tell other email servers around the world what to do with email coming from our domains (*umn.edu). There are three actions a DMARC policy can perform for unverified email:
- Reporting: No action is taken, but you are able to monitor where unverified emails are coming from within your domain
- Quarantine: Unverified emails are sent to the recipients’ spam folders
- Reject: Unverified emails are bounced back to the sender
Learn which policy the University is currently publishing.
How do I ensure my sent mail passes DMARC?
The University uses two methods to pass DMARC: 1) Pass by using either DKIM (Domain Keys Identified Mail) or 2) by using SPF (Sender Policy Framework) alignment.
- DKIM alignment requires the email sending source to have a private / public key pairing for the sending domain (@example.org / @umn.edu) and the email header "From:" domain needs to match that domain. (Preferred method)
- SPF alignment requires the email sending source to have an SPF record in University of Minnesota DNS (limited to only so many SPF records) and the email header "From:" / envelope from (a.k.a. "Return-Path:") domain needs to match the SPF record domain.
How do I know if the email I am sending is passing DMARC?
The University’s DMARC policy is set for only @umn.edu, @d.umn.edu, @r.umn.edu, @tc.umn.edu, @crk.umn.edu, and @morris.umn.edu. At this time we do not have a policy set for sub domains (e.g., math.umn.edu). You can check your email by sending an email message to [email protected], this will send an automated response indicating if it passed or failed DMARC. If you are unable to get an automated response, send an email to [email protected] and an email administrator will report back on your DMARC status.
Before the University moves to quarantine, we will be adding [UNVERIFIED] to the subject line to any mail that is not passing DMARC. This change will identify sources that need to become DMARC compliant before we update the policy to send mail to spam or bounce it back to the sender.